
How to Save Instagram DM Videos
Instagram Direct Messages (DM) are one of the best features of the popular photo-sharing app. While it’s great to receive messages from friends or family,…
Blogging & Tech Guides
Tips, tricks, and how-to guides on technology, social media and the internet.

Instagram Direct Messages (DM) are one of the best features of the popular photo-sharing app. While it’s great to receive messages from friends or family,…

So you have come across this term online and specifically on Instagram a lot, but you have no idea what it means, well in fact…
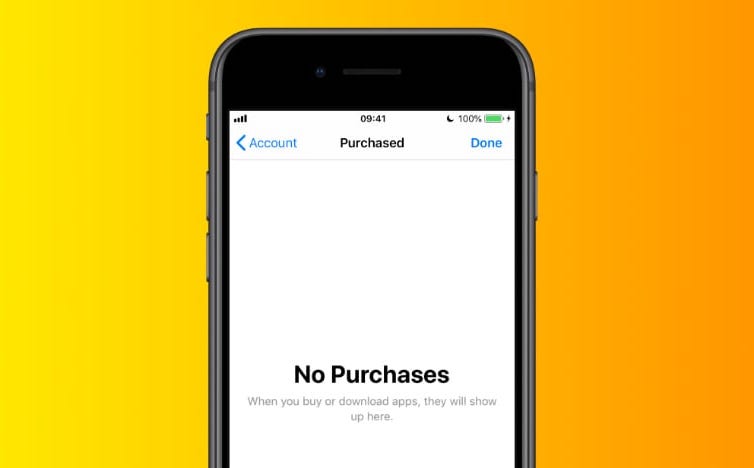
Deleting your purchase history will stop others from tracing your activities, but it won’t protect your credit card info. If someone finds out where you’ve…
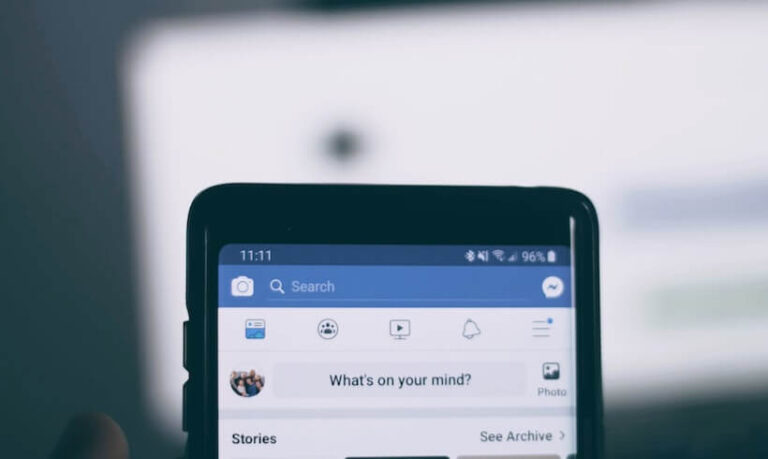
Facebook recently added a feature called “See all activities,” allowing users to view all the things they’ve liked or commented on across the social network.…
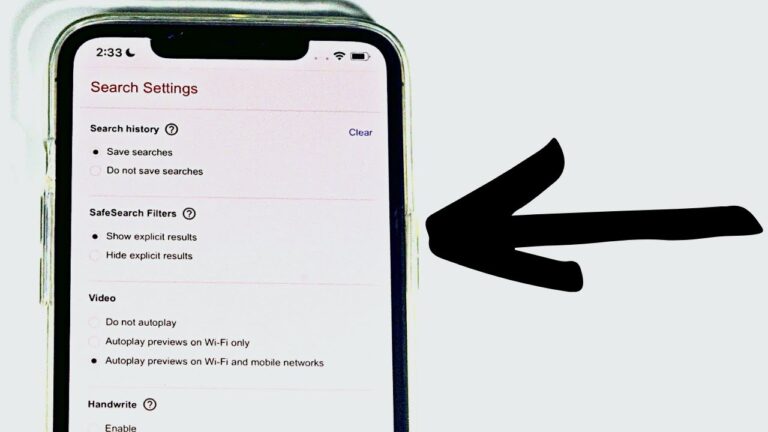
To turn off safe search, head over to google.com/account/safe-search and toggle the box next to “turn on safe search.” If you want to make sure…

Adobe Portable Document Format (PDF) is a widely used file format for creating and sharing documents. PDF documents can be password protected or encrypted with…

Looking to learn how to delete a Facebook group on an iPhone device, this is the right guide for you. With so many features to…
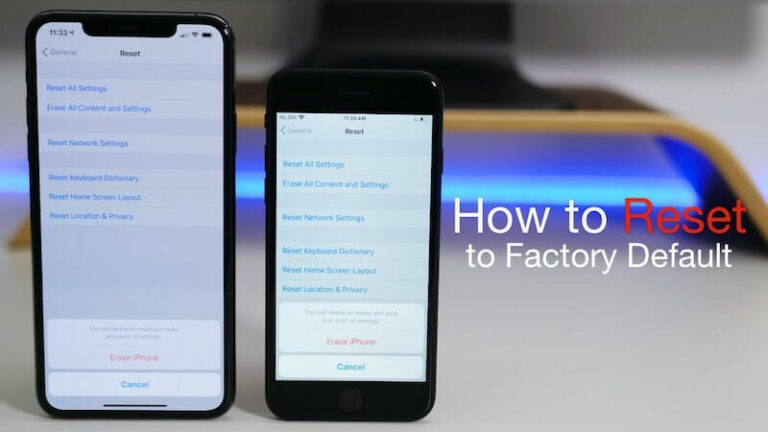
Factory resets are meant to wipe out everything on your device, including data, settings, and applications. This includes the operating system, which you’ll want to…

Instagram announced recently that it’s rolling out some changes to how people use the social network website. If you haven’t heard, Instagram is testing a…